CI/CD – Continuous Integration/ Continuous Deployment (Delivery) – is an approach to development that helps expedite the process of developing software with a large code base and multiple contributors while reducing errors. It accomplishes this by automating the process of integrating the code of different contributors and performing unit tests, ensuring that the code is fit for inclusion, or notifying the developer if there are any errors. Unit testing is great for identifying if there is any loss of functionality, but it does not test whether new security issues are introduced into the code base. That is where having a tool like Snyk helps.
What is Snyk and How Does it Fit into the Pipeline
Snyk is a security scanning tool that enables developers to test for vulnerabilities while developing instead of at the end of the development process, like in a waterfall-based SDLC. It changes the paradigm of security checking in the development of an application by making it an integrated part of the lifecycle, checked as frequently as desired.
Although Snyk provides a fairly robust cloud service that imports repositories for scanning, it is also available as a plugin for various code editors. The plugin enhances the testing of application code for security vulnerabilities allowing for real-time SAST (Static Application Security Testing). Further, suppose you already use a tool that manages your CI/CD pipeline, for example, Jenkins. In that case, Snyk already provides integrations that allow it to fit seamlessly into your existing pipeline.
Dashboard Information and How it Helps
No review of Snyk could be complete without considering what value it adds to the development process. Its true value becomes apparent when you have a look at its Dashboard.
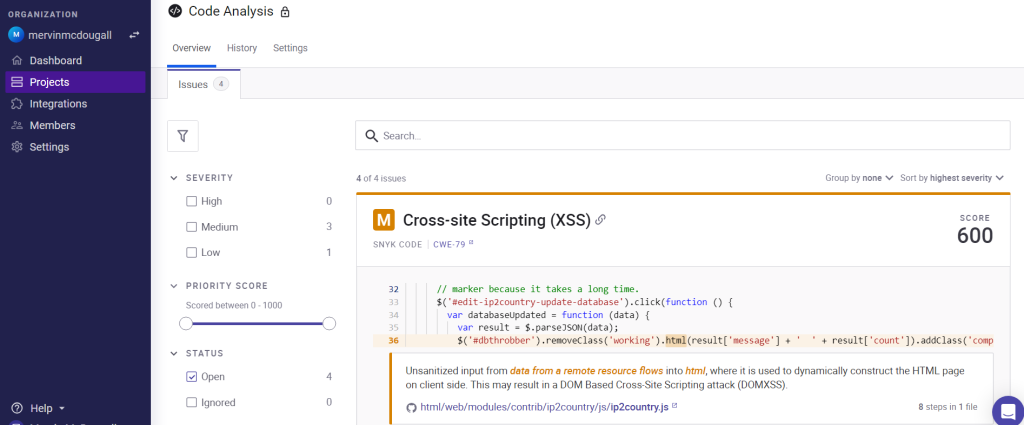
The screenshot above illustrates the sort of vulnerability breakdown delivered by this tool after scanning the repository. Consequently, if part of your process includes the preparation and delivery of a security package to stakeholders, the cloud service provides a means of analyzing the code and presents a detailed explanation of the vulnerability encountered and the recommended fix.
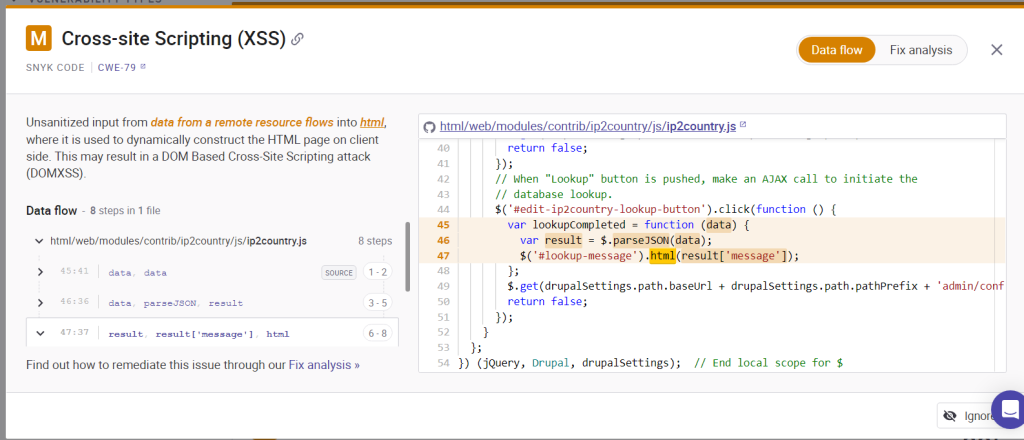
For example, for the Cross-Site Scripting (XSS) error identified above, it provided the following explanation:
Unsanitized input from data from a remote resource flows into html, where it is used to dynamically construct the HTML page on client side. This may result in a DOM Based Cross-Site Scripting attack (DOMXSS).
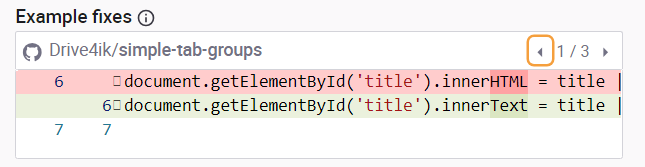
The accompanying fix analysis provides a recommended fix to the code.
The plugin provides a similar service when integrated into your editor. it scans the code for vulnerabilities and reports them.
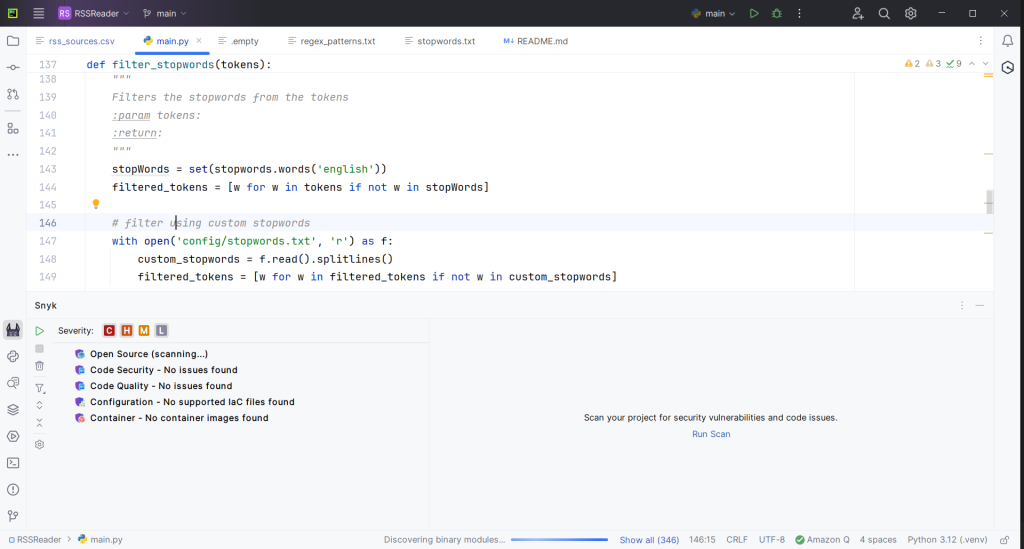
The Snyk panel at the bottom of my PyCharm editor illustrates the use of the scanning process as the plugin performs tests for critical, high, medium, and low-level vulnerabilities.
Snyk supports some of the more common web development functional languages. These include PHP, Python, JavaScript, Ruby, Scala, etc.
One feature that I have not explained but is available through the cloud service is the ability to send emails at intervals – daily, weekly, monthly – of a digest of all vulnerabilities discovered in the process of scanning. A feature like this can be used to alert specific stakeholders to changes in the code base which introduces vulnerabilities as they occur.
Closing Thoughts and Alternatives to Snyk
Snyk provides a balance of integrations for both coding editors and CI/CD tools. As a result, I believe it is a good addition to the CI/CD pipeline. Snyk offers a generous free package for small teams or individual developers before pricing begins. However, other services occupy this coveted space providing integrations for other pipelines and support for different languages. Some examples:
- Black Duck.
- Checkmarx.
- GitLab.
- GitHub.
- Mend.
- Invicti.
- Veracode.
- Aikido Security.
So, if Snyk doesn’t meet the muster, the other options might. But, I doubt you will be disappointed with Snyk.
Leave a Reply